Organizations are under pressure to protect their customer, financial, and other proprietary data from an increasing abundance of threats. Fines, increased public investigation, decreased customer loyalty, and reduced revenues are some of the costs for those who violate the rules.
In today’s always-on world where organizations may be negatively impacted by ransomware, cyber-attacks, IT disruptions, natural disasters and more, a confident, modern and unified approach to data protection is required across the entire digital business landscape.
Accutech believes that business resilience needs to:
After considering a lot of different strategies and approaches on how to automate Disaster Recovery processes, we saw an opportunity on investing once again on one of our trusted partners Veritas and its resiliency Platform.
We need a modern solution that delivers simplicity and ease of use with a unified management console spanning on-premises and cloud environments. Centralized management has been proven to increase staff productivity and begin to break down silos within organizations.
We can tailor the view across global environments by application, virtual machine, resiliency group and business service. From the centralized console, you can:
Also, the need for Disaster Recovery in the cloud is covered by having orchestrated, automated, at-scale disaster recovery to the cloud, multi-SLO compliance for complex multi-tiered applications. Last but not least, have ransomware protection with point-in-time recovery and with near-zero RPO.
Nevertheless compliance and performance work as a team and our customers needed to:
It’s an important aspect of your digital defenses from theft, sabotage and human error. However, not much is known to the wider public about the effectiveness of robust identity access management. In this article, we will take a closer look at this useful tool.
Employees, management, external contractors... not every user on an organization’s network is the same, both in terms of responsibilities and the trust afforded to them. This is the crux of the sophisticated concept of identity access management, also called IAM or IdM.
For security reasons, every user who logs onto the system needs to verify their identity – be they in-house workers, remote employees or external collaborators. Sophisticated verification tools allow the system to ask for credentials, including one or more ways to prove they are who they claim to be, before they verify these and grant access. IAM means holistic oversight of these roles, user accounts and settings, granting you full control of who can do what and how – or even when.
Multi-factor authentication is among the best practices in the field, as each user is expected to prove they are who they claim to be in more than one way, by providing something they know (e.g. a password), something they have (e.g. a token generator), and something they are (e.g. their fingerprint).
This strategy prevents bad actors from logging on with stolen information, as they are unlikely to have acquired more than one of the above. Thus, only authorized users can log on to the system, which is kept safe from intruders and prying eyes.
Privileged identity management and design looks at the needs of a company or other type of organization and creates roles for the users of its systems. For example, a lower-level employee needs to be able to access certain sets of data and certain applications on the organization’s system. He is given access to those, and nothing more.
Similarly, IT administrators need highly privileged access to be able to monitor the system, generate reports and adjust any settings. Therefore, their privileges are elevated.
Zero trust architecture is similar to sharing confidential information on a need-to-know basis. A zero trust model does not trust any user or device attached to the network by default, even if they were previously verified or are connecting from a known location. Instead, it calls call for mutual authentication each time, adding one more layer of security to your systems.
Accutech’s proven experience and expertise in IAM can help your organization function more safely and more efficiently. Give us a call or send us an email today.
In the digital era, the vital role of cloud-based setups is undeniable – especially so for businesses of all sizes looking to take full advantage of cutting-edge capabilities, and for those whose introduction to newer technologies has been sped up by the increase in remote working agreements.
Yet, private and public clouds combined into hybrid and multi-cloud environments come with new sets of challenges when it comes to data visibility and management, security, backup, recovery and overall resiliency.
The latter has been brought to the fore as an increasingly pertinent concern due to the rise in ransomware attacks and cloud-based apps.
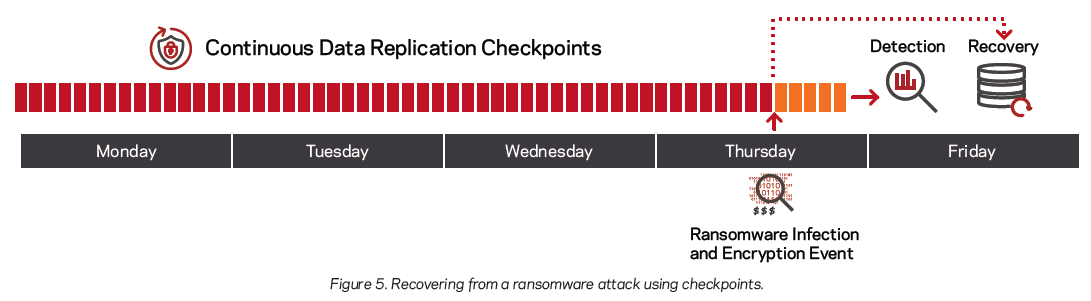
Resilience, also called resiliency, describes an organization’s capacity to bounce back after suffering disruptions, downtime and other incidents related to attacks and disasters. In the case of ransomware in particular, a resilient solution means the organization has at disposal recent replicated data to be used for recovery following a ransomware infection and encryption event.
Depending on the organization’s infrastructure and operational needs, various types of data replication policies are available. However, by far the most reliable strategy – and the one that Accutech coordinates for its clients – involves continuous data replication checkpoints.
This advanced option creates multiple checkpoints from a live data replication stream. In the event of data corruption or a ransomware attack, the latest healthy, uninfected checkpoint is used for recovery. The frequency of this intelligent replication cycle ensures that there is near-zero data loss even if the ransomware attack successfully encrypts the organization’s data, to hold it hostage.
This flexible solution is completely platform-independent. It is also ideal for multi-cloud environments. Despite having benefits, multi-cloud setups are rigid and can cause fragmentation, as workloads and applications are spread across on-premises locations, public clouds and private clouds. In such circumstances, you would normally be using different, separate tools to manage data and resiliency for each location – which means higher operational costs and human resources required, as well as increased likelihood for resilience gaps.
In response to this challenge, Accutech can set up a single-pane-of-glass resilience monitoring platform with real visibility – as well as manage it, if required.
This unified approach for your entire IT infrastructure, even when it’s spread across multiple clouds and on-premises data centers, will protect your data and workloads better, granting you increased confidence.
Resiliency in cloud computing comes with a new set of challenges, compared to traditional environments. Multi-cloud setups in particular add complications. Equipped with extensive experience in hybrid and multi-cloud setups and industry-leading tools, Accutech can make your organization more resilient with holistic, accurate solutions designed specifically for you.